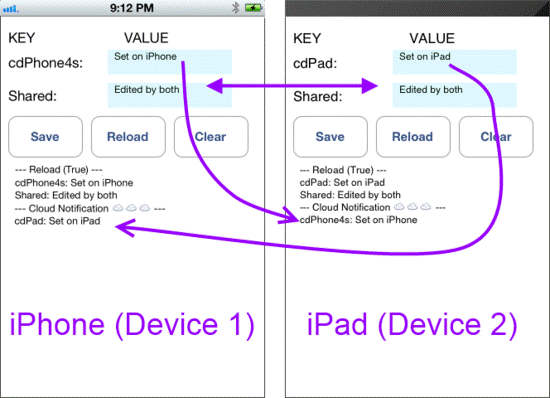
Apple introduced iCloud in iOS5 as a service to allow applications to store data on Apple’s servers and have it synchronized across all devices used by the same person (via their Apple ID). It also has a backup component. This document describes how to use some of the iCloud APIs provided by Apple to store and retrieve data from their servers, with C# samples for storing small key-value data pairs and for storing documents. It also discusses how iCloud Backup can influence the design of your application. The iCloud storage API in iOS5 allow applications to save user documents & application specific data to a central location and access those items from all the user’s devices. iCloud helps you store your photos, music, apps, documents, calendars and more. It’s an easiest way to manage your content. Apple has built iCloud functionality directly into many of their apps and iOS5. When you take a photo from your iPhone, it can automatically synchronize with iCloud, and be pushed to your iPad and Mac.
You can stop worrying about keeping all of your devices in sync once they are all linked to your iCloud account. Once you connect your device to the internet via a wired or Wi-Fi connection, all of your files will be automatically synchronized. The Backup feature allows you to store your personal data, along with music apps and books purchased from iTunes. You can restore all of your data directly to your device from iCloud, or move it to any new devices you buy. Apple has opened up development to third-party developers, which means that there will eventually be iCloud compatible apps for Windows aside those developed by Apple. Eventually iCloud development could spread to other platforms including Linux, Android, and BlackBerry. If you switch back and forth between a Windows PC and your Mac, it will not be long before you can keep both of them in sync with iCloud. You get 5GB of backup space for free, and there will likely be different pricing tiers based on how much data you want to store in iCloud. For $24.99 a year you get the Scan and Match feature, which scans your iTunes music library and adds any songs that are available in the iTunes library to your iCloud account. It does not matter if you purchased the songs from iTunes, from another music store, or ripped the CDs. All songs added to your iCloud account using the Scan and Match feature will be at 256kbps (DRM-free AAC files) regardless of the quality of your original track. There is a limit of 25,000 songs, but iTunes purchases do not count against that limit
iCloud Backup
While backing up to iCloud isn’t a feature that is directly accessed by developers, the way you design your application can affect the user experience. Apple provides iOS Data Storage Guidelines for developers to follow in their iOS applications. The most important consideration is whether your app stores large files that are not user-generated (for example, a magazine reader application that stores hundred-plus megabytes of content per issue). Apple prefers that you do not store this sort of data where it will be backed-up to iCloud and unnecessarily fill the user’s iCloud quota. Applications that store large amounts of data like this should either store it in one of the user directories that is not backed-up (eg. Caches or tmp) or use NSFileManager.SetSkipBackupAttribute to apply a flag to those files so that iCloud ignores them during backup operations. This article introduced the new iCloud feature included in iOS 5. It examined the steps required to configure your project to use iCloud and then provided examples of how to implement iCloud features.
The key-value storage example demonstrated how iCloud can be used to store a small amount of data similar to the way NSUserPreferences are stored. The UIDocument example showed how more complex data can be stored and synchronized across multiple devices via iCloud. Finally it included a brief discussion on how the addition of iCloud Backup should influence your application design.
Photostream:
Photo Stream is a service supplied with the basic iCloud service which allows users to store the most recent 1,000 photos on the iCloud servers up to 30 days free of charge. When a photo is taken on a device with Photo Stream enabled, it is automatically uploaded to the iCloud servers; from there, it is automatically pushed to the rest of the user's registered devices. The service is also integrated with Apple TV, allowing users to view their recent photos wirelessly on their HDTV. With Photo Stream, you can take a photo on one iOS device and it automatically appears on all your other devices, including your Mac or PC. Import new pictures to your computer from a digital camera, and iCloud sends copies over Wi-Fi to your iPhone, iPad, and iPod touch. You can even view recent photos on your big-screen TV via Apple TV. There’s no syncing, no email attachments, no file transfers. Your pictures are just there — on whichever device you happen to have handy.

Take a photo on an iOS device. Or import a photo from your digital camera to your computer. iCloud automatically pushes a copy of that photo over any available Wi-Fi or Ethernet connection to the Photos app on your iOS devices, iPhoto or Aperture on your Mac, and the Pictures Library on your PC. You can even view your Photo Stream album on your Apple TV. So you can show off your shots to friends and family from whichever device you’re using at the time.1000 of your latest photos. With you all the time.iCloud manages your Photo Stream efficiently so you don’t run out of storage space on your iPhone, iPad, or iPod touch. If you have Photo Stream enabled on your iOS device, every single photo you take appears in a special Photo Stream album that holds your last 1000 photos.
You can delete any photos you don’t want from the Photo Stream.1 To touch up a photo or keep a favorite shot permanently, simply save it to your Camera Roll. iCloud stores new photos for 30 days, so you have plenty of time to connect your iOS device to Wi-Fi and make sure you always have your most recent shots handy.1000 photos on your devices: New photos appear on your iPhone, iPad, or iPod touch in a rolling collection of your last 1000 photos.Save your best shots: If you take a photo you really love and want to make sure it stays on your iPhone, iPad, or iPod touch, you can save it from your Photo Stream to your Camera Roll.All your photos on your Mac or PC: Your computer automatically keeps all the photos that come through your Photo Stream.Master photo library. On your Mac or PC.
Keeping a complete set of your photos on your Mac is as simple as turning on Photo Stream in iPhoto or Aperture. Every new photo you take appears in a Photo Stream album just as it does on your iPhone, iPad, and iPod touch. But since your Mac has more storage than your iOS device, it automatically imports every picture from your Photo Stream into your photo library so you can edit, delete, and share the ones you want. Want to get the photos you’ve taken on your point-and-shoot or DSLR camera into your Photo Stream to view on all your other devices? The photos you import to your library from a camera or SD card are automatically uploaded to your Photo Stream. If you have a PC, you can auto-import and upload pictures, too. Just turn on Photo Stream, grab a camera, and start shooting.Make your photos a big deal with Apple TV.With Photo Stream and Apple TV, you can view your recent photos on your HDTV for some truly entertaining reality television.2 So you can, say, take pictures during your daughter’s softball game, then watch a photo play-by-play with the family gathered around the big-screen TV
References
http://www.apple.com/iphone/features/
http://www.quora.com/Whats-the-difference-between-the-cloud-cloud-computing-and-iCloud